Analysis of the Cambodian Huione Group’s 29.62 Million USDT Freezing Incident by Tether

Tether USD (referred to as USDT) is a centralized stablecoin issued by Tether Limited, pegged to the value of the US dollar and regulated through smart contracts on blockchain networks. Besides having the anonymous transfer and permissionless usage features of other cryptocurrencies, USDT gives the issuer significant control over the tokens. This control allows Tether to selectively issue or destroy USDT at specific addresses or restrict operations on particular addresses, a practice known in the industry as “Tether freezing.”
Such centralized freezing activities are typically triggered by enforcement requests from government agencies worldwide or by significant crypto security incidents. The goal is to stop known illegal activities involving USDT and intercept damaged assets to prevent further harm. As the adoption of USDT in the real financial system has increased, so have incidents of illegal activities involving cryptocurrencies. This rise has led to more frequent Tether freezing actions, significantly impacting many web3 enterprises that inadvertently receive risky crypto funds, causing business disruptions and potential legal risks.
This article analyzes the incident where 29.62 million USDT of the Cambodian Huione Group was frozen by Tether.
Overview of Huione’s Business Scale
Huione Group is a large financial conglomerate based in Cambodia, operating business segments including cryptocurrency wallets, payments, transaction guarantees, insurance, and a cryptocurrency exchange. Its core payment and guarantee businesses heavily use USDT. According to address tagging data from the on-chain risk fund monitoring management platform DeTrust under Bitrace, HuionePay and HuioneGuarantee have over 180,000 official and user addresses, making it the largest crypto enterprise in the region, influencing Southeast Asia and East Asia.
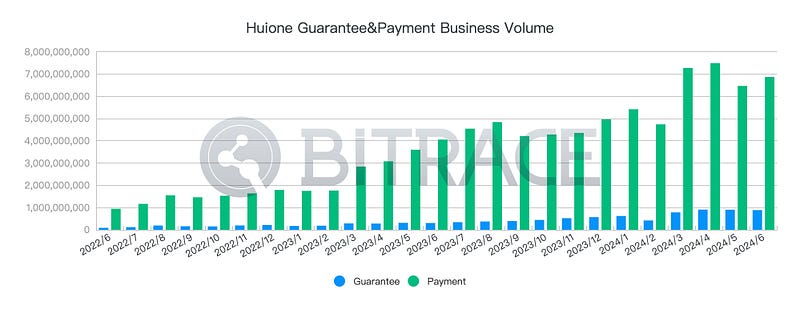
From June 2022 to June 2024, Bitrace monitored a steady rise in the monthly fund scale of all known HuionePay and HuioneGuarantee business addresses, from a low of 1.03 billion USDT in June 2022 to a high of 8.39 billion USDT in April 2024, totaling 102.397 billion USDT over two years.
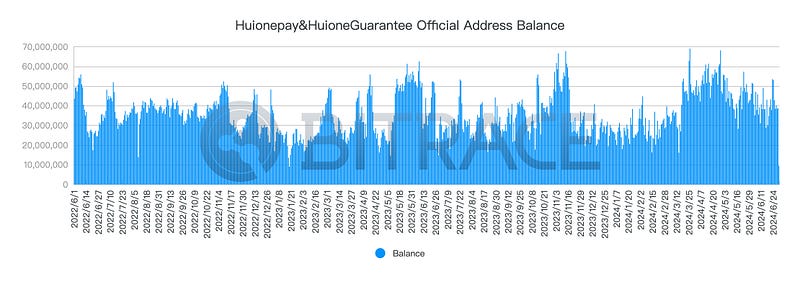
During this period, Huione-related business addresses maintained substantial reserves. From June 2022 to June 2024, the average daily balance of all known HuionePay and HuioneGuarantee business addresses was 35.68 million USDT.
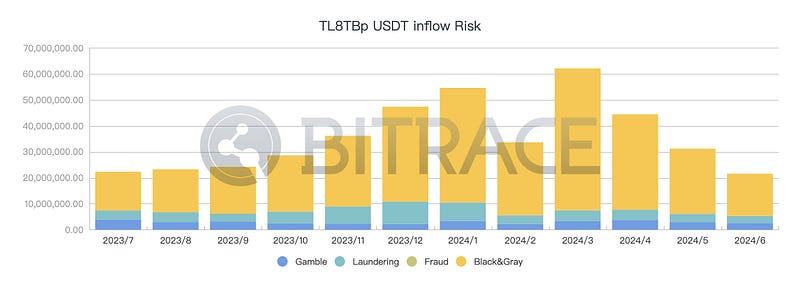
Given that Southeast Asia is a high-incidence area for illegal activities using cryptocurrencies, Huione’s business addresses were somewhat affected. For example, Bitrace monitored the core business address TL8TBp used by HuioneGuarantee, which had 2.158 billion USDT flowing in from July 1, 2023, to June 30, 2024. This included 0.35 billion in high-risk gambling funds (1.62%), 0.339 billion in high-risk black market transaction funds (15.71%), 0.054 billion in high-risk money laundering funds (2.50%), and 0.02 billion in high-risk fraud funds (0.09%).
Analysis of the Frozen Address Funds
On July 13, 2024, Tronscan showed that the TRON network address TNVaKW was restricted by Tether, with a substantial 29.62 million USDT frozen and unable to be transferred. Bitrace immediately launched an investigation.
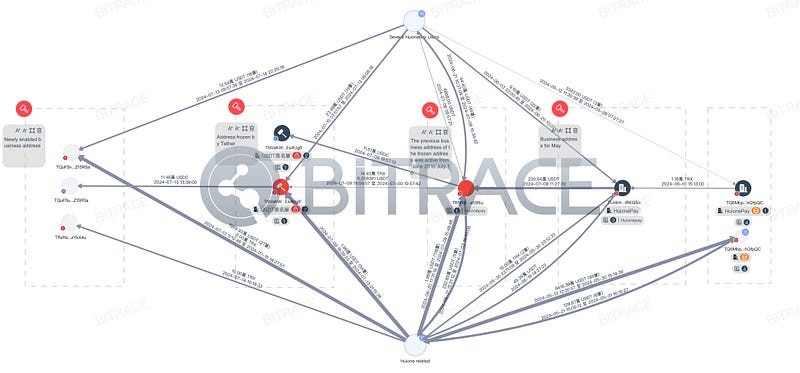
Preliminary investigation results showed that TNVaKW surpassed a transaction scale of 1 billion USDT within five days of creation, receiving deposits from numerous addresses marked as HuionePayUser on the TRON network, as well as funds from other HuionePay and HuioneGuarantee official addresses. Therefore, Bitrace confirmed this address as an official Huione business address and determined that the freeze was due to receiving a significant amount of stolen crypto funds.
The following day, the renowned on-chain detective ZachXBT revealed on social media that assets stolen from a Japanese exchange, DMM, had been transferred to HuionePay through cross-chain exchanges.
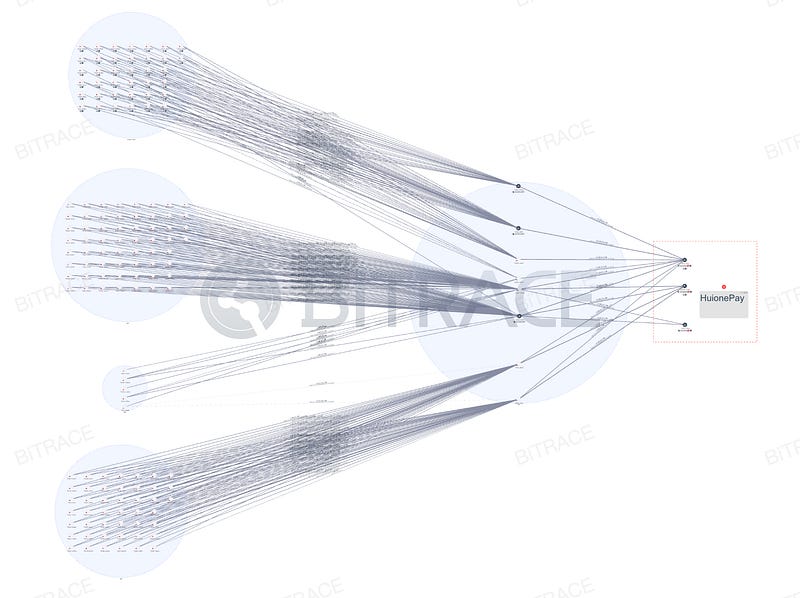
Using addresses disclosed by ZachXBT, Bitrace uncovered more addresses involved in laundering activities and reviewed the entire fund flow. Among the findings:
- 165 BTC crossed from Avalanche Bridge to Avalanche.
- 182 BTC crossed from ThorChain Bridge to Ethereum.
- 263 BTC crossed from Threshold Bridge to Ethereum.
The acquired tBTC and BTC.b assets were exchanged for approximately 31.82 million USD worth of USDT, USDC, and DAI on the Avalanche and Ethereum chains, then exchanged cross-chain to the TRON network, with around 14 million ultimately entering TNVaKW.
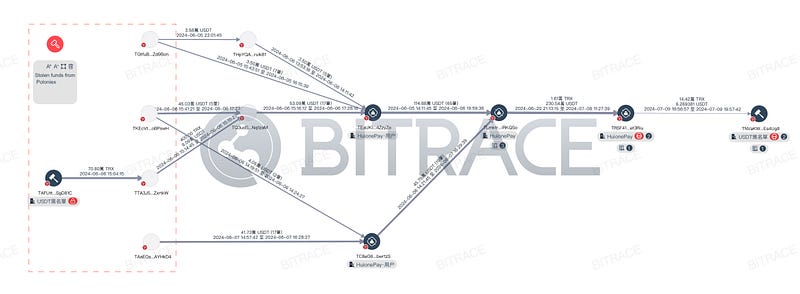
It is notable that DMM is just one publicly known security incident involving funds flowing into Huione addresses. In investigating other incidents, it was found that funds from the Poloniex exchange theft also connected to Huione. Between June 5 and 7, 2024, at least 1.05 million involved USDT flowed into HuionePay user addresses and subsequently into multiple HuionePay official business addresses, including TLmktr, TR5F41, and TNVaKW.
There is currently no direct evidence linking TNVaKW’s freeze to these two security incidents. However, considering that no other Huione business addresses were frozen, this suggests the freeze action was not targeted at Huione Group itself.
Analysis of HuionePay’s Run-on
As mentioned, the average daily balance of all known HuionePay and HuioneGuarantee business addresses is 35.68 million USDT. In the three months before the freeze incident, this value remained around 40 million USDT, meaning the 29.63 million USDT frozen accounted for 75% of its reserves, indicating some withdrawal pressure.
Analyzing the latest HuionePay business address TQuFSv:
This address was activated 2.5 hours after TNVaKW was frozen to handle HuionePay users’ deposit and withdrawal needs and received 114.8 thousand USDC from TNVaKW. As of July 16, 2024, 9:34:39, its transaction scale had reached 733 million USDT.
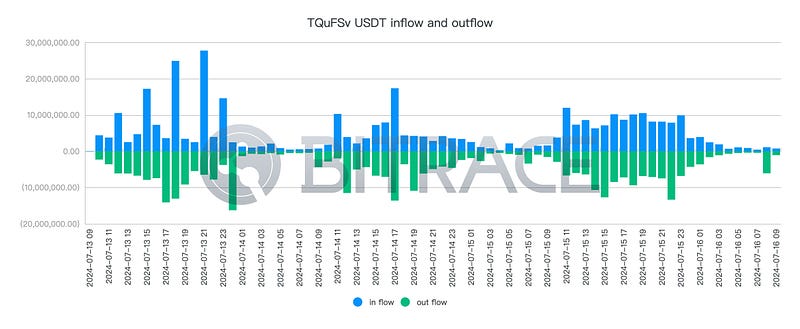
Hourly income and expenditure statistics for TQuFSv showed no significant fund abnormalities, and the address still had a balance of 12.88 million USDT.
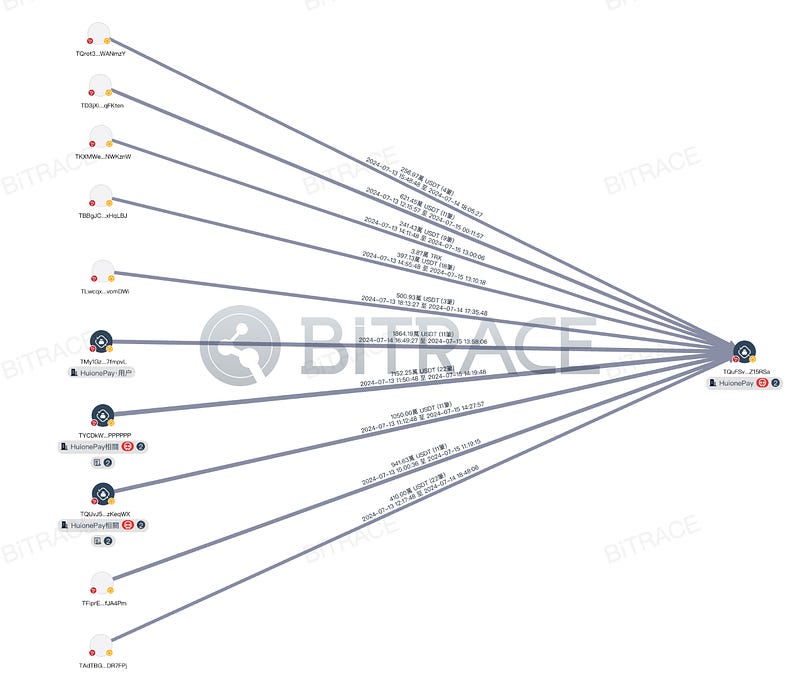
Analyzing TQuFSv’s counterparties, the top ten fund inflow counterparties contributed a total of 147 million USDT, including two addresses marked as HuioneGuarantee addresses, which transferred 73 million USDT and 15 million USDT, accounting for 23.64% of the total inflow. The top ten fund outflow counterparties received a total of 80 million USDT from TQuFSv, including three addresses marked as HuioneGuarantee addresses, which received 14 million USDT, 8 million USDT, and 6 million USDT, respectively, accounting for 7.76% of the total outflow.
This indicates that after the freeze incident, HuionePay experienced significant fund outflows, but the company promptly replenished reserves from other business addresses to meet user withdrawal requests.
Importance of KYT
For large-scale enterprises like Huione that use Crypto extensively, substantial fund throughput often attracts the attention of money laundering groups. With the global improvement in cryptocurrency-related law enforcement, the inability to identify the risk levels of platform users’ funds can impact business operations and even lead to investigation risks for operators.
Therefore, adopting professional KYT (Know Your Transaction) tools to accurately identify risky crypto funds and implementing necessary risk control procedures to handle platform risk events has become a critical consideration for crypto-involved enterprises.
Bitrace, through long-term tracking and research of the crypto crime industry chain, has established a unique data collection and processing system. We have built analysis models targeting typical crypto crime patterns and industry chains, dynamically expanding data labels through machine learning and pattern recognition algorithms. Currently, we have accumulated over 400 million address labels, including entity labels (exchanges, wallets, OTC, payment platforms, mining pools, DeFi, etc.) and exclusive risk labels (money laundering, online gambling, black/gray market, fraud, hacking, sanctions, freezing, terrorist financing, drug trafficking, etc.).
Additionally, the DeTrust on-chain risk fund monitoring management platform under Bitrace helps crypto-involved enterprises conduct 24/7 transaction monitoring of key business addresses, performing KYT and KYA on every new transaction and counterparty in real-time. It supports custom strategies to achieve dynamic risk assessment of transactions.
Compliance is the foundation of business operations. By establishing appropriate KYT and KYC procedures, enterprises can better meet local regulatory requirements and gain a competitive market advantage.
Contact us:
Website: https://www.bitrace.io/
Email: bd@bitrace.io
Twitter: https://x.com/Bitrace_team