Analysis of the Fake He Yi Twitter Phishing Scam and Cryptocurrency Theft

On June 14, 2024, Binance co-founder He Yi reported on social media that someone had impersonated her by creating a fake X account. The scammer used this account to send phishing links to victims, resulting in the loss of cryptocurrency assets worth 60 ETH. The post quickly garnered widespread attention.
Later that day, the victim contacted Bitrace for assistance. After investigation, the security team identified that the scam was linked to Inferno Drainer, a known phishing service provider. The affected group was rapidly expanding, with stolen funds exceeding $28 million. This article aims to reveal the details of the phishing techniques, the scale of the stolen funds, and the laundering channels used in this incident.
Phishing Techniques
Impersonating crypto celebrities on the X platform is a popular fraud tactic. Scammers use persuasive language to trick victims into submitting token authorizations through phishing links or downloading phishing applications, thereby illegally obtaining various crypto assets.
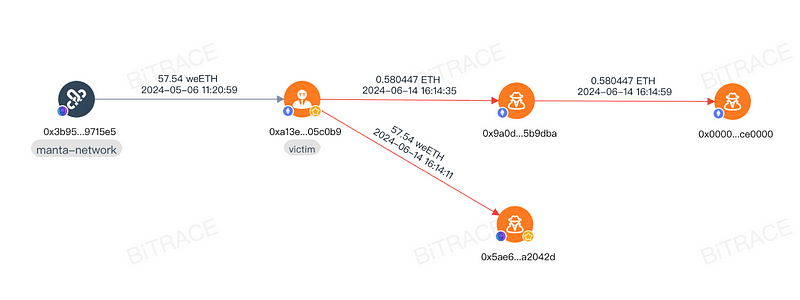
In this incident, the victim lost a substantial amount of funds, with more than $200,000 worth of Ethereum and Ethereum staking vouchers stolen. Specifically, 57.54 weETH was directly transferred to a phishing address and exchanged for ETH via a third-party DEX, while 0.58 ETH was moved through a phishing contract.
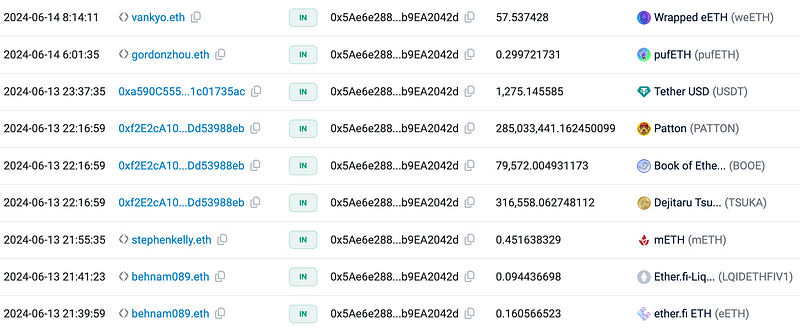
An audit of the scam address 0x5Ae6 revealed that this was a typical professional Drainer scam. The scammers quickly transferred valuable assets from the victim’s address upon gaining access. Besides Tether, assets issued by well-known protocols like EtherFi and Puffer were also targeted. As of now, the address still holds 197.78 ETH remaining from various ERC20 tokens, along with other tokens worth over $30,000.
Scale of the Stolen Funds
Tracing the transaction fees of 0x5Ae6 reveals a significant connection with 0x0000db5c8b030ae20308ac975898e09741e70000, identified by Bitrace and other security agencies as one of Inferno Drainer’s business addresses.
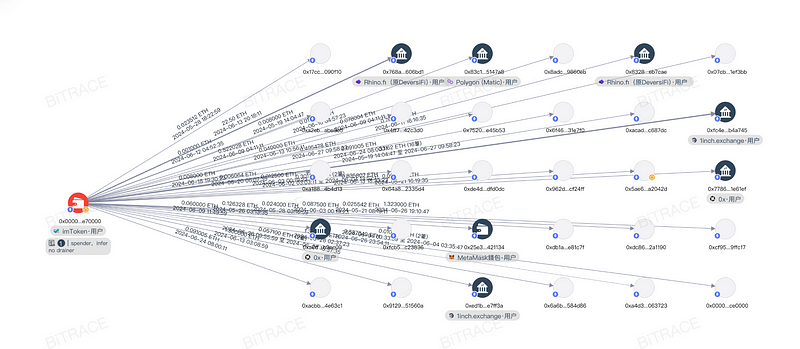
Over the past few months, e70000 has transferred funds to over 30 sub-addresses, including 0x5Ae6. These sub-addresses were widely used for various fraudulent phishing activities. Many incidents reported by community members on social platforms can be traced back to these addresses.
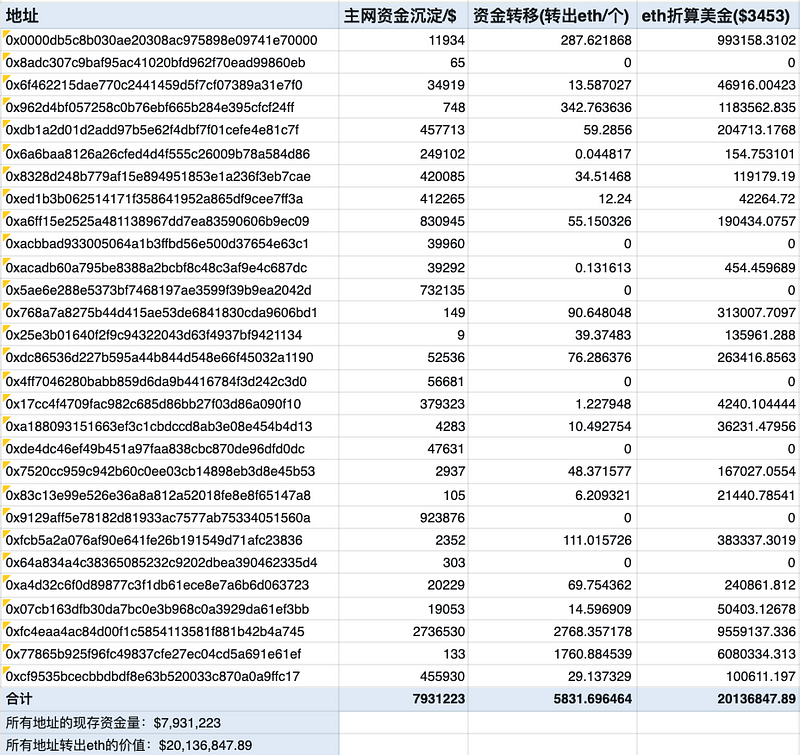
According to Bitrace’s security team, these addresses have illegally obtained over $28 million in various assets in the first half of this year alone. More than $20 million of the illicit gains have already been laundered. This figure might only represent the tip of the iceberg of the entire criminal network.
Money Laundering Methods
Compared to scammers targeting stablecoins like Tether, Drainers and their users display more “Crypto Native” characteristics in money laundering. They prefer converting illicit gains to ETH instead of more easily settled stablecoins, using centralized and decentralized platforms to obscure the funds’ destinations rather than traditional money laundering routes.
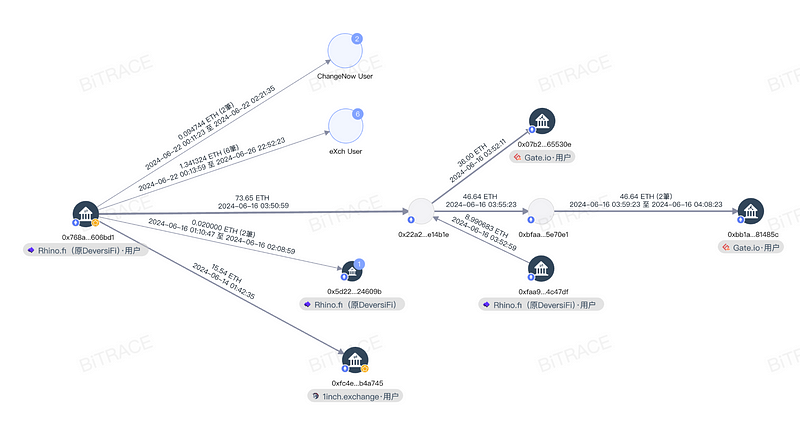
For instance, 0x768a used platforms like Changenow, eXch, RhinoFi, 1inch, and Gate extensively during the laundering process to hide the funds’ trail. Meanwhile, the address 0x5Ae6, which holds the illicit gains from this incident, has not yet started laundering the funds. Bitrace will continue to monitor this address, seek to intercept the funds, and help victims recover their losses.
Finally, a reminder to all investors: always verify the official website or social media accounts of a project before making any transactions to avoid phishing attacks.
Contact us:
Website: https://www.bitrace.io/
Email: bd@bitrace.io
Twitter: https://x.com/Bitrace_team