Are Hardware Wallets 100% Safe? 2 Types of Fraud You Need to Know About

Hardware wallets are physical devices designed specifically for storing cryptocurrencies. They are considered a critical tool for securely storing crypto assets, as they use built-in secure chips to store private keys offline, ensuring users retain full control over their digital assets. Since hardware wallets typically operate offline, they reduce the risk of being targeted by online hackers.
However, despite this strong security, a large number of fraud incidents targeting less knowledgeable users have occurred, leading to the loss of assets stored in hardware wallets. This article introduces two common types of hardware wallet fraud: the hardware wallet manual scam and the hardware wallet tampering disguise scam.
Hardware Wallet Manual Scam
This type of fraud revolves around exploiting the general lack of understanding about how to use hardware wallets. Fraudsters replace the original manual with a fake one, misleading victims into transferring funds to phishing addresses. Victims purchase hardware wallets from third-party e-commerce platforms, open the package, and follow the instructions in the “manual” to set up the wallet, using the “initial PIN” and backing up the “mnemonic phrase” printed in the manual. After transferring a large amount of funds to the wallet address, the assets are stolen.
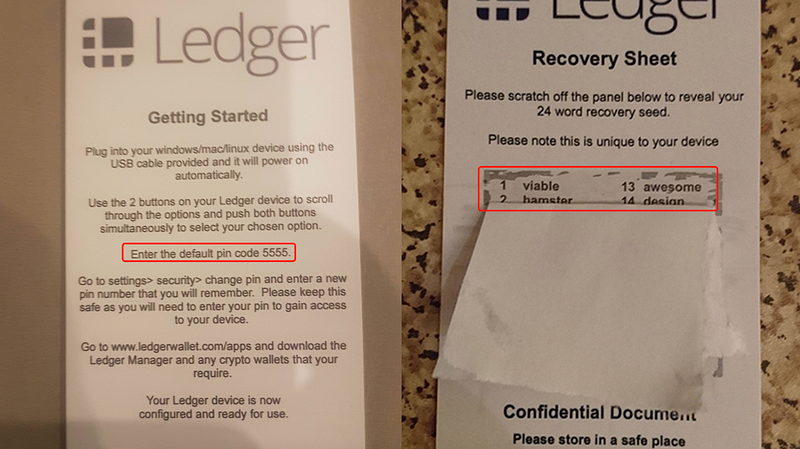
The root cause of this is not that the hardware wallet has been physically hacked but that the fraudsters had activated the wallet beforehand, obtained the address’s mnemonic phrase, and replaced the manual. The pre-activated hardware wallet is then sold through unofficial channels. Once the target transfers crypto assets to the address, the funds are stolen as part of the standard fraudulent wallet process.
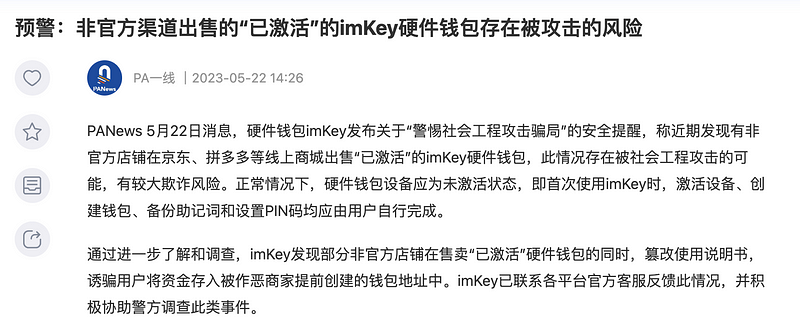
Similar risks also exist in the secondary market in Mandarin-speaking regions. A well-known hardware wallet manufacturer, imkey, issued a warning about discovering some unauthorized stores selling “pre-activated” hardware wallets with tampered manuals, deceiving users into depositing funds into wallet addresses previously created by malicious sellers. Thus, recognizing official e-commerce stores is as important as identifying the official website.
Tampered Hardware Wallet Devices
A Ledger user received a package containing a brand-new Ledger X hardware wallet and a letter, despite not having made an order. The letter claimed that due to a cyberattack, Ledger had experienced a data breach, and as a result, they were sending affected customers new hardware wallets for security purposes.

However, the authenticity of the letter was doubtful. Pascal Gauthier, CEO of Ledger, clearly stated that the company would not provide compensation for the accidental leak of personal data. The user suspected a scam, shared more pictures, and showed the internal plastic casing of the wallet, which clearly had signs of tampering.
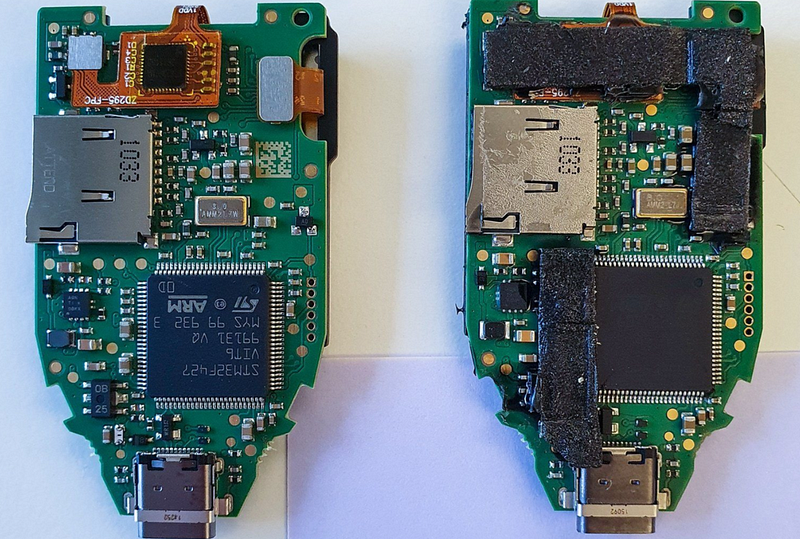
Additionally, Kaspersky’s security team reported a case involving a counterfeit Trezor hardware wallet. The victim purchased a Trezor Model T from an unofficial channel, but the device had been altered by the attacker, with its firmware replaced to allow access to the user’s crypto assets, facilitating theft.
Final Thoughts
The above cases show that supply chain attacks targeting hardware wallets are widespread. Both ordinary investors and hardware wallet manufacturers should remain vigilant. Proper usage can effectively mitigate the risk of theft:
- Buy hardware devices from official channels
Any hardware wallet purchased from unofficial channels is not secure. - Ensure the wallet is in an unactivated state
Officially sold hardware devices should be in an unactivated state. If a device is activated or the manual includes an “initial password” or “default address,” stop using the device immediately and report it to the official hardware wallet manufacturer. - Generate addresses personally
Apart from the device activation process, setting up the PIN code, generating the binding code, creating addresses, and backing up the mnemonic phrase should all be done by the user. Any step performed by a third party exposes the user to financial risk. Under normal circumstances, hardware wallets should be unactivated, meaning users must activate the device, create the wallet, back up the mnemonic phrase, and set the PIN code themselves.
If any hardware wallet users suffer losses due to such social engineering attacks, please contact Bitrace immediately. We will assist you in recovering assets through legal means. For more anti-fraud knowledge, download the 2024 Web3 Anti-Fraud Handbook by Bitrace. Download link: https://bitrace.io/zh/blog
Contact us:
Website: www.bitrace.io
Email: bd@bitrace.io
Twitter: @Bitrace_team
LinkedIn:@bitrace tech