Bitrace Insight: User Self-Verification of Fund Legitimacy Will Become More Common

Recently, a well-known KOL’s account was subjected to risk control and failed to lift the freeze despite appeals. The KOL exposed a chat record with a customer service representative from a certain exchange on social media. In the screenshots, the customer service agent requested the KOL to provide documents such as payslips, bank statements, and tax returns to prove the legitimacy of the funds in the account, sparking a community debate.
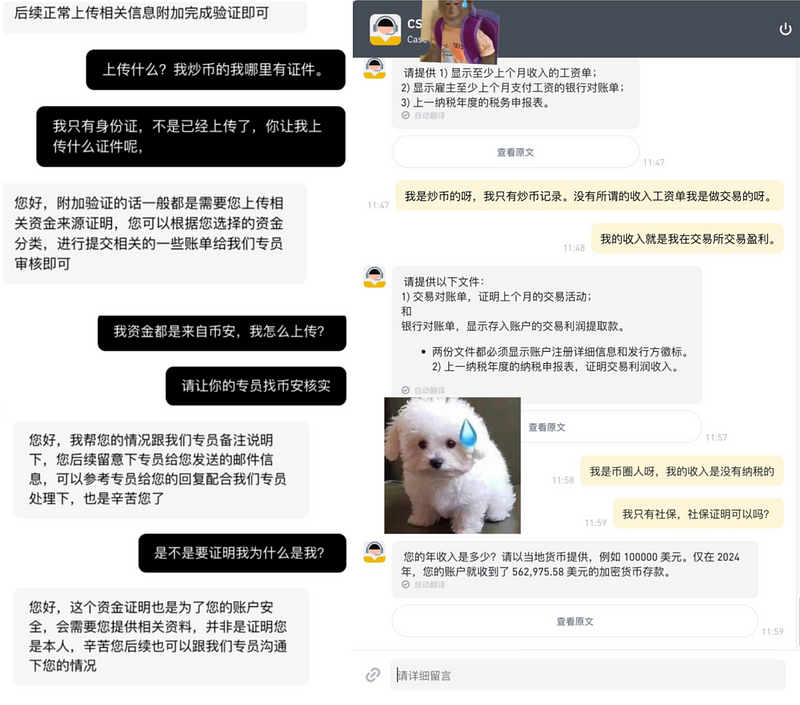
In fact, such risk control measures are not without reason. Even after completing identity verification (KYC), the source of a user’s funds may still trigger platform restrictions.
Why Proof of Fund Sources is Required
Proof of asset source, a centralized review behavior, may be triggered either because the exchange deems the user’s account suspicious or due to law enforcement requests from government agencies worldwide or temporary crypto security incidents. The goal is to investigate suspected illegal activities involving cryptocurrency, intercept damaged assets, and prevent further losses. If it is determined that a user’s funds are linked to illegal activities, restrictions will be imposed.
Funds Originating from Sanctioned Addresses
Take TornadoCash, a sanctioned coin mixing platform, as an example. OKX CEO Star once emphasized, “If users deposit funds from sanctioned entities like Garantex or TornadoCash into their OKX account or withdraw funds to such addresses from OKX, the compliance risk control mechanism will be triggered, leading to account closure.”
Bitrace studied the relationship between OKX users and TornadoCash. As of August 9, 2024, after conducting a rapid audit of four active TornadoCash routing addresses, it was found that 42 OKX user addresses received funds directly from TornadoCash, involving 45 transactions totaling 345.5 ETH.
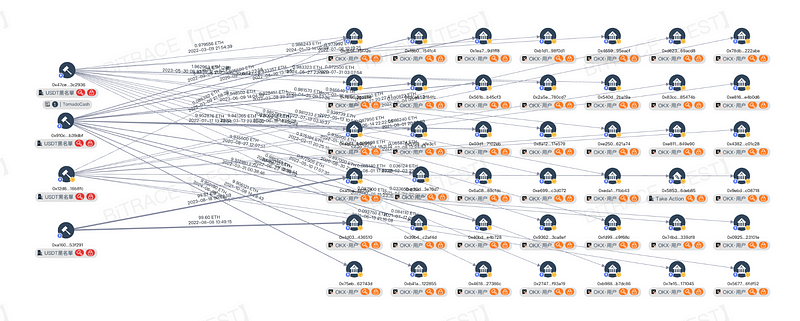
The anonymity of on-chain addresses makes it difficult to verify whether the entity corresponding to a sanctioned deposit address matches the identity information of the OKX account holder. It’s challenging to confirm whether the user knowingly deposited risky funds. In such cases, exchanges require users to provide “proof of fund sources” to assess whether the user was unknowingly involved, determining the legality of the funds before deciding if further risk control measures are necessary.
Funds Related to Real Cases
Take the most common fake wallet app theft cases as an example. The Bitrace analysis team used the BitracePro on-chain analysis tool to track the hashes provided by the victims and discovered that the hacker converted part of the BNB into 46,000 USDT via PancakeSwap, then divided the funds into four transactions for further laundering. One of the transactions was sent directly to the Transit Swap Exploit hacker address, while the other three went to different Binance user addresses for cashing out.
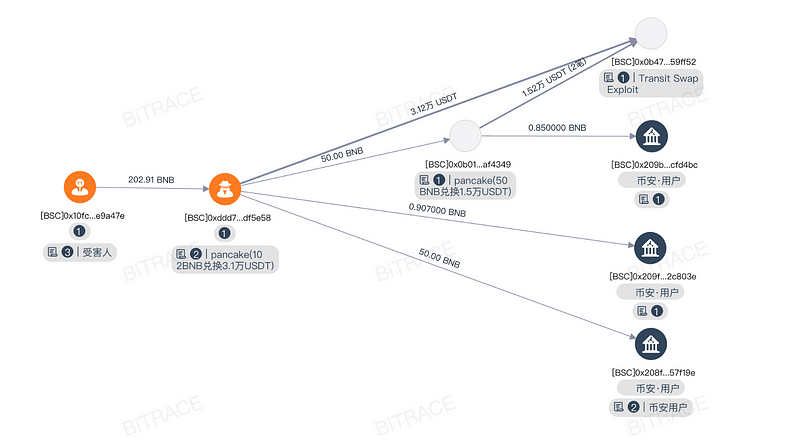
When criminal funds flow into centralized institutions like exchanges, the exchange, in line with compliance obligations, may restrict the relevant accounts, prompting them to request “proof of fund sources” from suspicious users to verify their legitimacy. If a suspect attempts to launder illegal funds through the exchange, this measure can intercept the stolen funds tied to real cases, preventing further losses to the victim.
Centralized exchanges, as one of the most crucial infrastructures in the industry, have long been the primary victims of fund contamination by criminal entities. The above cases are not exhaustive. In reality, crypto AML measures are often more complex and are essential steps for the industry to move toward compliance.
KYT: Reshaping the Security Boundaries of VASP Operations
According to statistics, $24.2 billion of the total cryptocurrency transactions in 2023 were linked to illegal activities. Against this backdrop, VASPs must enhance their anti-money laundering capabilities to ensure safe operations and compliance with international and local regulations.
For example, Binance, a well-known exchange, is committed to complying with AML and CTF (Counter-Terrorist Financing) regulations to protect user safety. To fulfill these regulatory obligations, Binance collects user information and documents under certain circumstances to verify the source of their funds and assets.
Thus, in addition to conducting basic KYC identity verification, VASPs need to implement deeper verification — KYT (Know Your Transaction). This means not just knowing the user’s real name but also understanding their on-chain behavior:
- Fully utilizing technical tools and data analysis to create profiles of users’ fund addresses, layering users based on their on-chain interactions and fund sources, applying stricter monitoring and restrictions to high-risk users to prevent risky funds from contaminating the platform and affecting other users.
- Integrating external threat intelligence data, issuing alerts or temporary payment freezes when users transfer funds to risky or involved addresses, preventing fraud or legal investigations from reaching platform users.
While requiring suspicious users to provide “proof of fund sources” may increase VASP’s operational costs or trigger user dissatisfaction in the short term, in the long run, this will be key to protecting brand reputation, maintaining user trust, and avoiding legal risks.
Contact us:
Website: https://www.bitrace.io/
Email: bd@bitrace.io
Twitter: @Bitrace_team
LinkedIn:@bitrace tech