Risks of Illicit Funds in Crypto Privacy Transfers

In the information society, data security and privacy protection have become unavoidable topics for everyone. Whether in financial transactions, identity authentication, or blockchain applications, we all face the same core challenge: how to prove that "something is true" without revealing any additional information.
Zero-Knowledge Proof (ZKP) is the cryptographic theory developed precisely to address this problem.
As a cryptographic technique, it enables the verification of the truthfulness of a statement without disclosing the underlying information itself. The concept was first proposed in 1985 by Shafi Goldwasser, Silvio Micali, and Charles Rackoff from MIT in their seminal paper "The Knowledge Complexity of Interactive Proof Systems."
The core idea of this theory is that Zero-Knowledge Proofs (ZKP) have three fundamental properties: completeness, soundness, and zero-knowledge.
- Completeness: If the statement is true, an honest verifier can be convinced that the honest prover indeed possesses the correct information.
- Soundness: If the statement is false, no dishonest prover can convince an honest verifier that they possess the correct information.
- Zero-Knowledge: If the statement is true, the verifier learns nothing beyond the fact that the statement is true.
There are two main types of zero-knowledge proofs:
- Interactive Zero-Knowledge Proofs: The prover and verifier interact multiple times until the verifier is convinced of the proof.
- Non-Interactive Zero-Knowledge Proofs: The prover generates a proof once and gives it to the verifier, with no further interaction required.
The importance of this theoretical framework has been steadily increasing in enhancing privacy and security in blockchain, cryptocurrencies, and decentralized finance (DeFi).
Tornado Cash represents one of the most successful practical implementations to date. Operating as a cryptocurrency mixer across multiple blockchains, the protocol provides indiscriminate anonymity by obfuscating the origin, destination, and counterparties of funds, enabling nearly untraceable transfers of various tokens to different addresses.
In the operational mechanism of Tornado Cash——
When making a deposit, a user first generates a secret value and submits its hash together with the deposit amount to the smart contract. Upon receiving the deposit, the contract records the corresponding commitment in the deposit list.
Later, when the user initiates a withdrawal, they provide the smart contract with a zero-knowledge proof demonstrating that they possess a secret matching one of the unused commitments in the deposit list. After the smart contract verifies the validity of the proof, it transfers the corresponding deposited amount to the user-specified withdrawal address.
From the perspective of external observers, it becomes impossible to determine which specific deposit the withdrawal originated from. This significantly increases the difficulty of tracing funds on-chain and effectively strengthens the privacy of blockchain transfers.

According to monitoring data from the cryptocurrency regulatory technology firm Bitrace, the operational addresses of Tornado Cash received a total of 693,412 ETH tokens during 2025, with an aggregate value of approximately $2.5 billion. Clearly, despite the earlier OFAC sanctions turbulence, the protocol has not been fully suppressed and continues to maintain significant influence within the industry.
Furthermore, with multiple public mentions by prominent figures including Ethereum co-founder Vitalik Buterin, the on-chain privacy transfer protocol Railgun has also experienced a substantial increase in transaction depth and overall activity.
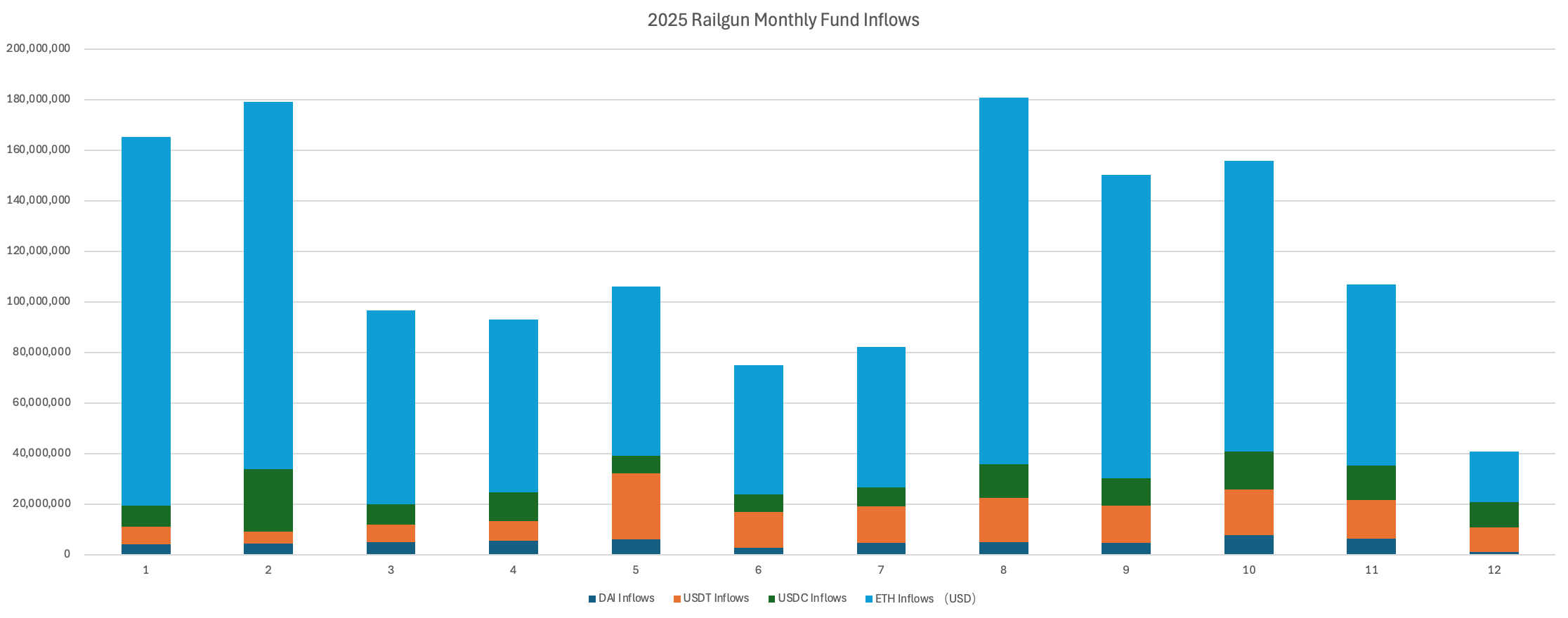
According to monitoring by Bitrace, in USD terms, the protocol recorded a net inflow of $1.4 billion in 2025, with inflows predominantly driven by ETH tokens. This indicates that, at least within the crypto-native community, industry participants exhibit a stronger demand for Ethereum-based privacy transfers compared to stablecoins.
Caution regarding the financial threats posed by privacy protocols to Web3 entities.
Cryptocurrency adopters have a natural and legitimate pursuit of privacy. However, as adoption deepens, malicious actors increasingly exploit cryptocurrencies for illegal and criminal activities. Hacking groups, including state-sponsored entities such as Lazarus, have extensively utilized privacy protocols like Tornado Cash to launder illicit proceeds, thereby obscuring the origin and destination of funds. This has directly resulted in sanctions and usage restrictions imposed by major global law enforcement agencies (or formerly imposed) on such protocols.
For centralized Web3 institutions, this presents not only legal risks associated with exposure to illicit funds but also significant compliance challenges in their operating jurisdictions.
Bitrace, a regulatory technology firm based in Hong Kong, has long collaborated with law enforcement and regulatory authorities in major countries and regions worldwide. The company investigates cryptocurrency-related cases and incidents, continuously monitors the use of crypto infrastructure by illegal industries such as online gambling, money laundering, darknet/black-market transactions, and fraud. With a comprehensive threat intelligence database and rapid response mechanisms, Bitrace assists clients in effectively perceiving, predicting, identifying, and countering threat funds to mitigate potential legal risks.
Contact us:
Website: www.bitrace.io
Email: bd@bitrace.io
Twitter: @Bitrace_team
LinkedIn:@bitrace tech


