The Northern Myanmar Alliance Army Extorting Cryptocurrency?

The Northern Myanmar Alliance Army Extorting Cryptocurrency? On-chain AML Tools Uncover the Truth Behind Addresses
On January 16, 2024, a blogger on a Chinese social media platform exposed that the Myanmar Alliance Army is suspected of forcibly collecting large amounts of cryptocurrency from Chinese nationals stranded in Myanmar who are involved in telecom fraud activities. The blogger also displayed cryptocurrency addresses purportedly used for the payments. This revelation has since gained significant traction online.
This article, jointly produced by Bitrace & MistTrack, analyzes the disclosed cryptocurrency addresses, including the transaction patterns, the risk of the fund sources, and the activities of related addresses, aiming to disclose the relevant analytical content.
Address Behavior Analysis

The original text mentioned, “***Grabbing Chinese people everywhere, then sending them uniformly to the Qingshuihe Baisheng Hotel, asking if they would pay for their own safety. The premise for paying for their own safety is to hand over 500,000 yuan in person, and the alliance army would then send them to Wabang Nandong. Later, the price dropped to around 300,000 yuan.” Based on this, researchers conducted a USDT exchange rate analysis on the disclosed receiving address TKFsCN, attempting to deduce the settlement unit behind specific amounts of USDT payments.
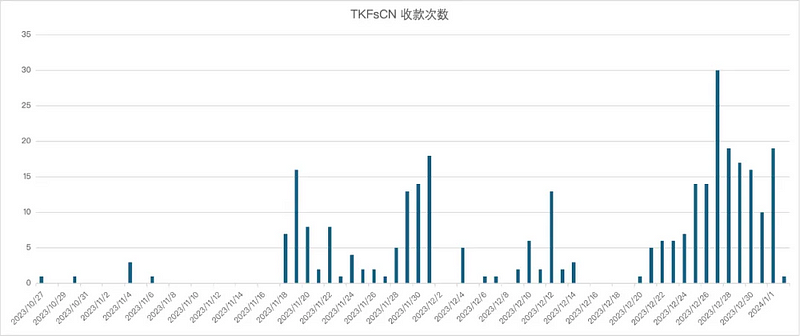
The historical transaction records of the receiving address show that the single USDT transactions received by this address include many non-rounded amounts, such as 71417, 42857, etc. This is common in scenarios where transactions are settled in currencies other than USD. After attempting to calculate using exchange rates of various major fiat currencies to USDT, researchers found that these transactions appear to be settled at an exchange rate of 1 USD to 7–7.2 RMB. Additionally, the amounts of funds transferred in a single transaction tend to cluster in the ranges of 500,000–600,000 RMB, 1,000,000 RMB, and 1,500,000 RMB.
After filtering out transactions of 100 USDT or less, statistics show that out of a total of 307 USDT deposits into the address TKFsCN, 193 were in amounts consistent with the RMB to USD exchange rate, accounting for 62.86% of the total transactions and 45.29% of the total transaction amount.
This indicates that more than half of the transactions received by this address are settled in RMB, with a significant number of deposits being in the amount of 500,000 RMB. Therefore, it is likely that the party paying the USDT is Chinese.
Source of Funds Analysis
The original text mentioned, “After occupying the old street, they also grabbed (note: Chinese people involved in telecom fraud activities) everywhere, asking if they were willing to pay for their own safety. Those who paid could be sent away, while those who didn’t would be sent to China.” If this is true, the transactions involving TKFsCN should show a significant number of new counterparties, with funds partly originating from addresses related to black and gray market activities, money laundering, and fraud.
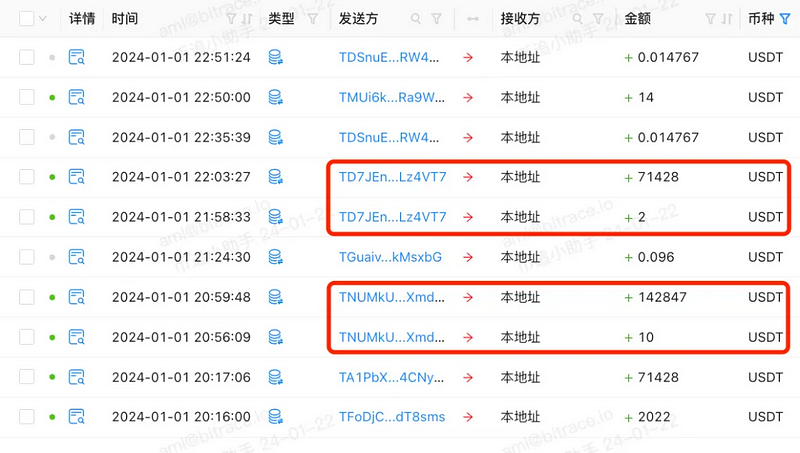
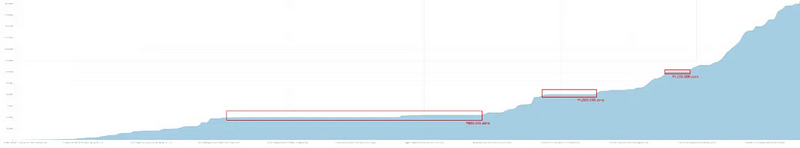
Data shows that between October 22, 2023, and January 2, 2024, TKFsCN received USDT transfers from a total of 182 direct counterparties. Among them, 117 addresses exhibited a pattern of consecutive small and large amount transfers. This is a typical transfer testing behavior, where the payer verifies the correct address by not transferring the entire amount in one go. This indicates that at least 62.29% of the counterparties might be making their first transaction with TKFsCN, rather than being regular trading partners.
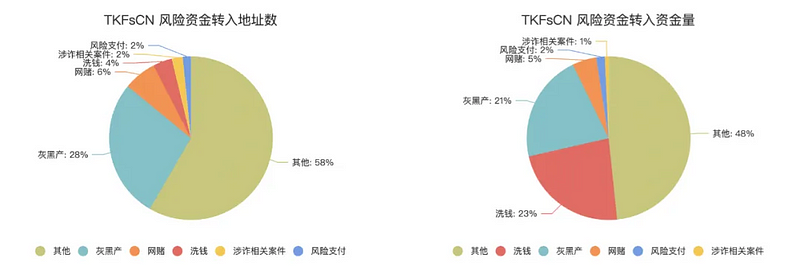
A deeper address risk fund audit of TKFsCN reveals that the counterparties transferring funds to this address are closely associated with black and gray market activities, online gambling, fraud, money laundering, and risky payments. Among the 182 direct depositors, as much as 42% are addresses related to risky activities, transferring a total of USDT worth $33,523,148 to TKFsCN.
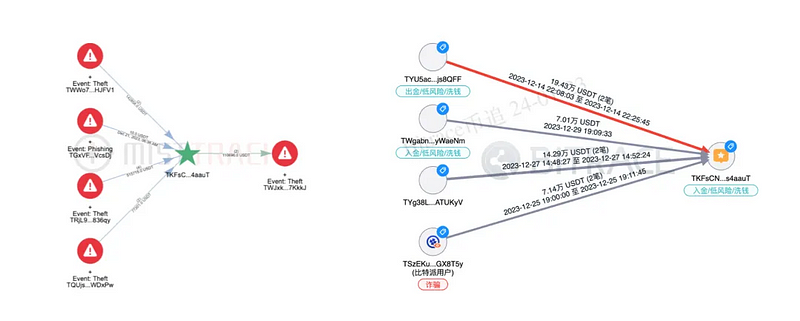
It is noteworthy that among these risk activity-related addresses, investigators also identified seven addresses explicitly linked to known criminal cases, including two money laundering cases, one fraud case, one online gambling case, and one telecom fraud case. The suspects’ geographic locations are all in northern Myanmar or Cambodia.
This indicates that the counterparties initiating payments to TKFsCN are not only involved in numerous high-risk crypto activities but also closely connected with criminals in Southeast Asia.
Another peculiar point is that investigators found a money laundering address associated with a telecom fraud case among the outgoing addresses, suggesting that the fund flow analysis of some outgoing addresses also raises certain questions. These questions will be non-sensitively expanded upon in the following section, “Related Address Analysis.”
Related Address Analysis
Clustering analysis based on the TKFsCN address reveals that this address is likely part of a cluster involving nearly one hundred addresses. Some of these addresses not only exhibit similar fund receipt and payment activities as TKFsCN but also reveal more information about the recipients. Taking TKKj8G as an example:
- TKKj8G directly received a total of over 4.6 million USDT from TKFsCN in 6 transactions, making it one of the collection addresses in the subsequent fund chain.
- TKKj8G is one of the core receiving addresses, with 50 out of 60 receipts of amounts over 100 USDT exhibiting similar small-amount testing behavior as seen with TKFsCN.
- TKKj8G has been active since August 18, 2023, much earlier than other addresses, and during this period, it engaged in transactions with Huione Guarantee, receiving 160,000 USDT from a Huione Guarantee address, behaviorally indicating that a merchant of Huione Guarantee was retrieving a deposit from Huione Guarantee.
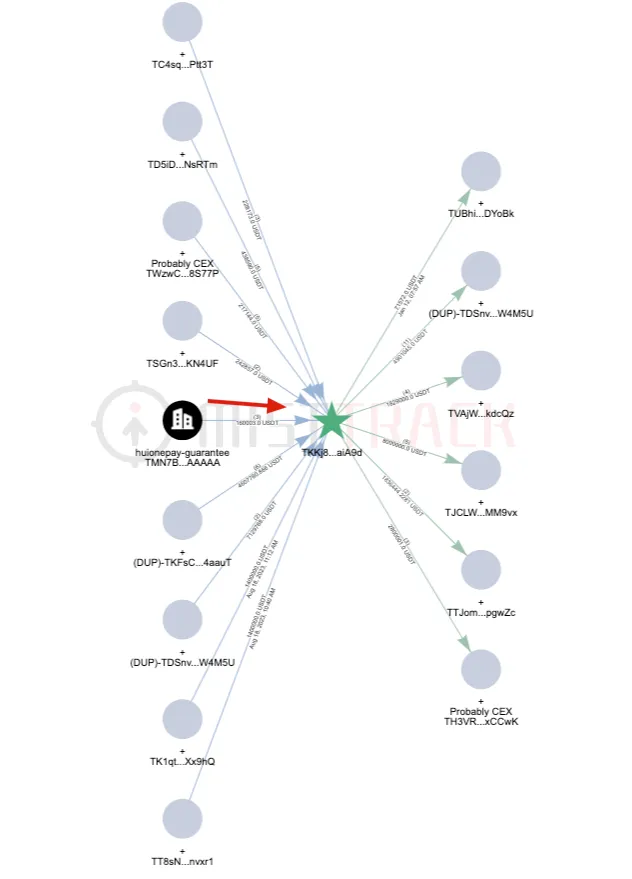
This suggests that the so-called “Finance Department Address” mentioned in the original text may not actually exist. Instead, the addresses, including TKFsCN and TKKj8G, likely belong to a digital currency exchanger based in northern Myanmar or Cambodia, who is collecting these funds on behalf of others for certain reasons.
Suspicious Transactions
In summary, investigators can easily outline a typical payer profile: the address owner is engaged in illegal activities in Southeast Asia and, for some reason, has to pay 500,000 RMB worth of USDT to a collecting address. Since it is their first transaction, they conduct a small test transfer before making the large transfer to prevent errors. The cryptocurrency used for payment either comes from their illicit earnings or is purchased from other illegal entities.
However, not all payers fit or fully fit this profile. Investigators also identified some addresses that do not match these characteristics, such as TYU5acSGRwsYJfBhdpQc3broSpfsjs8QFF —
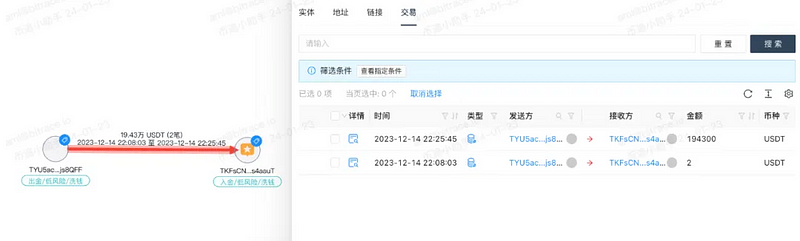
This address is one of the seven directly involved addresses mentioned earlier. The other six addresses transferred cryptocurrencies worth 500,000 RMB, 500,000 RMB, 1,000,000 RMB, 1,000,000 RMB, 2,700,000 RMB (1,500,000 + 1,200,000), and 550,000 RMB to TKFsCN. However, the transfer amount from TYU5ac was converted to 1,360,000 RMB at the same exchange rate. Despite being a round number, this particular amount is significantly different from the other addresses.
Investigators could not determine the reason for this discrepancy. Considering that this address exhibited small test transfers, a reasonable hypothesis is that the transaction from this address represents a consolidated transfer of three payments worth 500,000 RMB each, with a 10% discount applied.
Summary
This article provides an in-depth analysis of publicly disclosed addresses, focusing on transaction patterns, fund source risks, and activities of related addresses. The key conclusions are as follows:
- More than half of the transactions received by the target analysis address are settled in RMB, with significant transfers in amounts equivalent to 500,000, 1,000,000, and 1,500,000 RMB.
- The counterparties transferring funds to the target analysis address are closely associated with black and gray market activities, online gambling, fraud, money laundering, and risky payments.
- Before receiving these funds intensively, the target address and its related addresses already showed signs of risky business activities. Clustering analysis of the target address suggests that the cluster may be linked to a merchant of Huiwang Guarantee.
- The addresses initiating payments to the target analysis address are closely connected with criminals in northern Myanmar or Cambodia.
In conclusion, some of the revelations in the article “The Alliance Army’s Cryptocurrency Account Exposed, Extorting Billions in Virtual Currency from People in Northern China” align with on-chain facts. Indeed, many individuals involved in the Chinese telecom fraud industry in northern Myanmar or Cambodia are collectively transferring USDT assets in round RMB amounts to a set of addresses. However, these addresses may not be the so-called “Finance Department addresses” but rather belong to local digital currency exchangers, differing from what was stated in the original article.
Contact us:
Website: https://www.bitrace.io/
Email: bd@bitrace.io
Twitter: https://x.com/Bitrace_team